The following steps show how to perform public-key encryption:
- Generating the public key,
- Using the public key to generate the private key,
- Encrypting the text into ciphertext, and
- Decrypting the ciphertext into the original text.
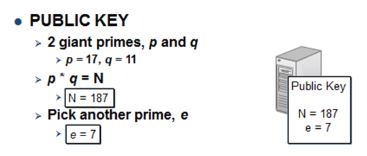
| First, pick two random giant prime numbers. This example picks two small primes to keep it simple: 17 and 11. Multiply them to get 17×11 = 187. Pick another prime: 7. That is our public key including two numbers, 187 and 7. |
|
Pick p = 17 and q = 11 ⇒ p×q = 17×11 = 187 = N ⇒ Public key is (N=187, e=7)Generating the Private Key
Pick an algorithm, modular arithmetic in this example, to generate the private key from the public key.
One of the modular arithmetic examples is 38 = 2 (mod 12)38–2 = 36 |
|
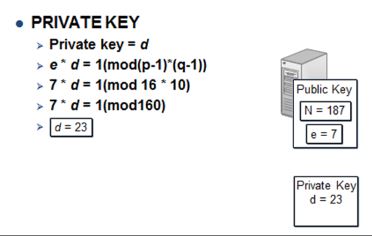
e × d = 1 ( mod (p–1)×(q–1) ), the algorithm used = 7 × d = 1 ( mod (17–1)×(11–1) ) ∵ e=7, p=17, q=11 = 7 × d = 1 ( mod 16×10 ) = 7 × d = 1 ( mod 160 ) ⇒ Private key d = 23
|
My friends will ask me, “Hey, since you were adopted, would you ever consider adoption?” I’m like, “Yes. Absolutely. If I ever have kids, I want them to go to a good home.” — Jamie Ward |