|



|
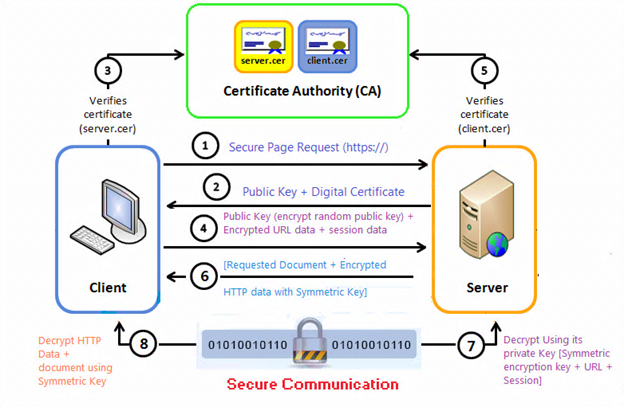
It performs the following eight steps:
- Secure page request (https://...), where HTTPS (Hyper Text Transfer Protocol Secure) is the secure version of HTTP, and all communications between your browser and the website are encrypted.
- Public key + digital certificate, where digital certificate is a digitally signed document that serves to validate the sender’s authorization and name. The Certification Authority (CA) attests that the sender’s name is the one associated with the public key in the document.
- Certificate verification (server.cer), where server certificates (server.cer) are basically used to identify a server. The CA verifies identity and legitimacy of company that requested a certificate and if the verification is successful, CA issues signed certificate.
- Public key + encrypted URL data + session data, where the browser then uses the public key to encrypt a random symmetric encryption key and sends it to the server with the encrypted URL required as well as other encrypted HTTP data.